When it comes to business industries that have witnessed constant expansion over the years, the healthcare industry likely pops up in mind. The global healthcare enterprise software sector is growing at a rate of 13% and is expected to be worth USD 76.45bn by 2025.
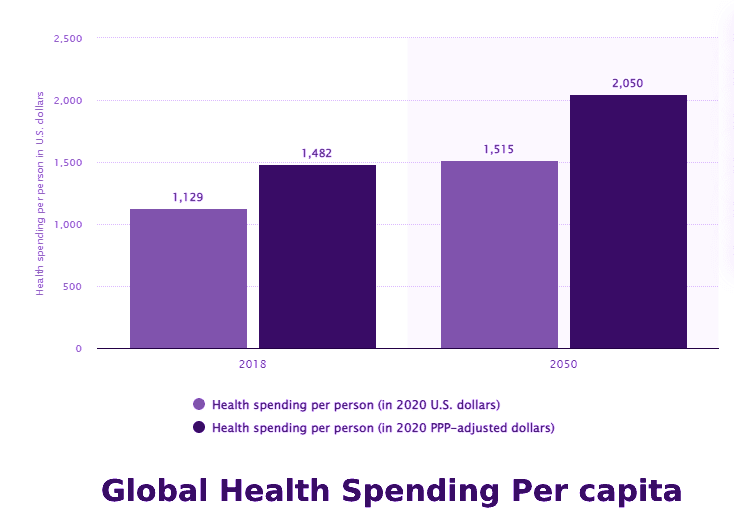
Meanwhile, Statista estimates that the total healthcare spending per individual in the United States will rise to USD 1,515 by the year 2050.
Healthcare concerns started rising due to Covid-19 and this resulted into digitalization globally. Besides, the pandemic also made healthcare personnel spend on advanced tech to keep up with the rising competition.
However, developing software that meets healthcare requirements is a promising but challenging endeavor. Following the latest industry trends and complying with HIPAA is a non-negotiable part of SDLC (software development lifecycle) in the healthcare domain.
This guide aims to offer you a detailed insight into HIPAA and how to get started with HIPAA Compliance Software Development.
What is HIPAA?
HIPAA, or the Health Insurance Portability and Accountability Act of 1996, is one of the many federal data protection laws in the US. The law protects patients’ healthcare data in every form by introducing significant sets of standards and rules. Do not disclose this data without the patient’s prior permission or consent.
Healthcare organizations related to PHI (Protected Health Information) should take the required measures to ascertain the privacy of patients’ health data that aligns with HIPAA requirements.
HIPAA compliance is mandatory for all organizations developing a medical e-prescription system, medical web app system, or any other software in the medical domain.
Why should Healthcare Businesses develop HIPAA Compliance Software?

1. Protects the healthcare data of patients
Data privacy incorporates the patient’s personal details, medical information like lab reports, medication, and payment-associated data that shouldn’t be disclosed. But, in certain situations, a patient’s electronic health record (EHR) can be shared or accessed with their prior permission.
2. Safeguards the electronic data of patients
HIPAA ensures that the patient’s PHI is stored securely and uses different encryption techniques for data transportation over a safe channel.
3. Maintains a secure administrative structure
This makes it easy to access health data securely in one centralized repository. A few defined standards under HIPAA include:
Structured classification
The medical records get bifurcated structurally into the below-listed categories:
- Procedures
- Diagnosis
- Medication
- Lab reports
- Equipment and suppliers
Exchange of electronic data
Transmission of electronic data between parties to conduct financial or administrative activities should include correct information. For instance, medical insurance companies might request information for claim settlement. Hence, it must include all the accurate information to boost communication efficiency between the two parties.
Rules of operations
This defines a particular set of regulations for operating which information should or shouldn’t be incorporated for electronic data transmission. These regulations make administrative transactions safe and secure.
Special identifiers
Each health record has a distinct identification key. For instance, a ten-digit National provider no. or an employee identification no.
4. Transferable health insurance
HIPAA covers the existing health concerns of employees within their health insurance coverage. That implies that the employer can’t exclude any current health issues from the employee’s insurance plan. Similarly, it also allows employees to register for group health insurance plans in case of uncertain events or coverage loss.
5. Prevents healthcare abuse and fraud
With additional security rules, the Act provides authority for preventing healthcare fraud, individual abuses, and data breaches.
Which Medical Software Development Companies Need HIPAA?
Any medical software company that shares, collects, or holds the patient’s private health data that will be used for treatment needs HIPAA compliant software development.
Three key factors determine if you need to follow HIPAA-compliant app development:
- What kind of entity would use the healthcare software?
- What kind of data the healthcare app will store/share/use?
- What kind of software will be used?
Kind of User Entity
As per HIPAA, there are essentially two kinds of entities that need to comply with the HIPAA law:
1. Covered Entities
HIPAA defines covered entities as people who work directly with the patients such as insurance providers, hospitals, or physicians.
2. Business Associates
These entities are responsible for collecting, storing, sharing, and processing health data. For instance, a custom medical software company that creates software/services for the healthcare domain. That also includes third-party facilities the software may use, like hosting, cloud services, etc. These should be HIPAA compliant as well.
Both business associates and covered entities risk losing millions of dollars as a penalty for developing non-HIPAA-compliance software development. Hence, both organizations must ensure their product is HIPAA-compliant. To protect the PHI and comply with HIPAA, business associates and covered entities should sign proper business associate contracts.
Kind of Data
All the rules under HIPAA, like security and privacy rules, are based on the kind of data which needs to be protected – PHI. That can be defined as medical data conveying a patient’s identifiable details. PHI is different from other medical information as it is personally identifiable. For instance, test results of a patient’s heart rate or blood sugar levels.
PHI is developed, shared, and used while providing healthcare/medical services to a patient. This data can be in different forms, like billing information, physical health records or any other electronic form. When the PHI appears in electronic form, it is referred to as an ePHI. However, it is important to protect and encrypt ePHI carefully, just like physical data.
Kind of Software
The final aspect that determines if building HIPAA-compliant software is necessary is the kind of technology used in that software. Unauthorized people shouldn’t have the liberty to modify or access the ePHI in the developed software. Here, an accurate authorization will ensure that the integrity of the PHI remains protected.
Moreover, HIPAA compliance software vendors should conduct audit controls to track any modifications to the PHI. That further helps the software developers to check potential risks and identify significant information in case of a breach.
The software should have access controls for protecting who can view the PHI. Some controls that can be implemented are emergency access protocol, automatic timeout, and identity proof for authentication.
Software vendors should launch a unique authentication before letting anyone access the software containing PHI. Be it through a key card, complex password or fingerprint scanner; there should be high security maintained than a conventional app.
Besides initial authentication, the software vendors should develop a process that retrieves ePHI if the main access point gets damaged. PHI’s classified and important nature implies that there should be a data retrieval method in case of an emergency.
And lastly, the software should automatically log off or timeout when a user remains inactive after a certain time of being logged in. This feature will ensure no unauthorized individual can access the ePHI when the computer’s user steps away from it.
Which Medical Software Development Companies Don’t Need HIPAA?
Not all software or app developed for the healthcare industry needs to be HIPAA-compliant. The main question that keeps apart those apps that fall within HIPAA from those that do not is – Does the app hold or collect PHI that any covered entity will use during treatment?
If your answer to this question is a yes, continue reading to know what measures you should take for building HIPAA-compliant software. However, if your answer to the above question is a no, you don’t need HIPAA-compliance software development.
A few organizations have developed software containing PHI, but that data cannot be shared or transmitted with any covered entity. A good example here can be certain kinds of wellness tracking watches and bracelets. Based on the type of data stored in those apps and how safely that data is held, they might not have to comply with HIPAA.
What are the Rules of HIPAA Compliance?
HIPAA compliance for software development involves meeting the HIPAA requirements and related rules, legislation, and amendments. Ideally, HIPAA is strict (involving several rules and heavy penalties) and generous (giving liberty to apply the many rules in the best way possible).
HIPAA defines five key rules that every healthcare software app should follow:
The Privacy Rule
This rule was designed for protecting the disclosure and use of healthcare records and any other PHI. It is intended to enhance the health data flow in a manner that limits theft and fraud. The rule grants patients a few rights to their health data. That includes the right to receive a copy, examine, and request modifications to their health records.
The Security Rule
The HIPAA Security Rule puts forth criteria to protect ePHI that’s created, received, utilized, or maintained by any covered entity. As per this rule, the covered organizations should implement adequate physical, technical, and administrative safeguards to ascertain the security, integrity, and confidentiality of ePHI.
Though HIPAA doesn’t always state the exact or minimum requirements, the NIST resource guide for implementing the HIPAA Security Rule can be referred to for guidance.
The Enforcement Rule
The rule sets forward how the HHS (Department of Health and Human Services) enforces the HIPAA law. The regulators determine the liability and calculate penalties in the event of a non-HIPAA-compliant app development. Typically, the investigations begin from a breach of data or a complaint. However, the HHS retains its right to probe even without any trigger.
The Notification Rule
This HIPAA rule creates an alert by sending notifications to all business associates and entities if any PHI breach occurs. The HHS defines what makes a breach depending on the extent and nature of the involved PHI, the kind of disclosure, if the data was seen, and the exposure risk.
Notifications to all the affected people should be sent within 60 days of the day the breach was discovered. If the breach involves over 500 individuals, the organizations need to issue a proper media notice.
The Omnibus Rule
The HIPAA Omnibus Rule modifies many HIPAA Security, Enforcement and Privacy rules. This rule is much more stringent than others, making it difficult to neglect data breach notification. It also extends stricter non-compliance liability to the business associates and institutes new privacy limits for PHI use.
Compliance over and above HIPAA
HIPAA is one of the many security and privacy laws that could apply to new software. Be sure to keep a tab of other requirements at the industry, global, federal, and state levels.
There will be severe consequences if you avoid any HIPAA compliance software development restrictions. Hence, it is crucial to understand how you can develop HIPAA-compliant medical software.
What are the Basic Features for HIPAA Compliant Software Development?
An organization should take all necessary precautions to safeguard patient data according to PHI regulations. HIPAA-compliant app development can be done using any tech solution. However, there are a few basic requirements that fall under the HIPAA-compliant guidelines. Those include:
The Technical Preventive Measures
These measures concentrate on the significant features for technical safety. PHI should be secured according to NIST standards to avoid data breach and transmitted over firewall security. Below are some significant features:
- Unique user identification
- Authorized user access
- Data backup for emergency conditions
- Integrity and safeguarding
- Security of the data transmission
- Encryption of data
The Preventive Features (Physical)
The Preventive Features (Physical) focus on accessing PHI physically, regardless of the location. PHI can be securely stored in external clouds, servers or other electronic data systems. Besides, it protects mobile devices and other hardware from unauthorized access. A few significant features of preventive security include:
- Data backup and recovery in contingent situations
- Access control to authorized employees/users
- Proper record storage and maintenance
- Physical safety of the PHI storage devices
Media and Device Controls
The healthcare personnel should handle how the secured ePHI is removed/disposed /transferred from devices if the system has been sold/re-used or a user leaves the organization. Enlisted are the important features that fall under media and device control.
- Re-use of ePHI
- Proper regulation of ePHI
- Automation of data storage and retention
- Employee accountability to protect information
The Administrative Security Measures
A few guidelines are unavoidable for businesses that manage health-related data. Hence, such businesses need to follow mandatory guidelines when they work with the management of health-related data. The administrative security measures keep a check on HIPAA guidelines and policies that a business follows.
There are many administrative activities that should be performed for maintaining administrative security. Some of them are:
- Introducing risk management procedures and policies.
- Appointing security officers to perform a regular risk assessment.
- Train employees on identifying possible cyber-attacks and ways to prevent them.
- Strict restrictions should be maintained for ePHI accessibility.
- A contingency plan should be developed to protect the ePHI integrity.
- Periodic data backups and data recovery management should be maintained.
How to Develop HIPAA-Compliant Software?
The five major HIPAA rules discussed above give a general idea of data privacy and security. However, in reality, healthcare organizations and software developers need to follow a proper HIPAA compliance checklist for software development.
Conduct Risk Assessment
Before building HIPAA-compliant software, it’s important to determine your compliance level and conduct a risk assessment. That should include defining risks and threats to your organization, IT infrastructure, and policies to recognize any loopholes in compliance. You should specifically look at the following:
- Where the PHI is collected, stored, or transmitted
- Employee training
- Data management
- Evaluate current security practices created to protect PHI
- Access potential damage in case of PHI breach
- Document the risk assessment details and develop an action plan to enhance security processes
Next, list specific features and policies for a successful HIPAA-compliant software development process.
Focus on Data Storage and Minimization
If the data incorporates ePHI, you should host it on a remote or on-premise service with a signed BAA (Business Associate Agreement). Many big cloud storage service providers like Google Cloud, Microsoft Azure or AWS are already well-acquainted with HIPAA.
The best data security practices are created around data minimization. Hence, collect only the data that’s important for the current task and nothing extra. In the case of HIPAA-compliant software development, this implies not gathering PHI unless it’s necessary.
Don’t Forget Data Encryption
Encryption is a crucial way business associates, and covered entities can prevent a breach of data. The mHealth apps and healthcare software can comply with HIPAA’s Security Rule that needs ePHI to be encrypted with adequate physical, technical, and administrative safeguards.
The data in HIPAA compliance solutions need to be encrypted in-transit and at-rest. Meanwhile, the decryption tools should be saved at a different location or device per NIST guidelines.
Maintain Robust Data Backup and Disaster Recovery
The Security Rule also presents a need to maintain robust data backup and recovery plans. For a mHealth app to comply with these requirements, a policy should be formulated for where and when to backup PHI or any other important data.
The data is typically stored in a mirrored or remote cloud facility in order to maintain the uptime. Remember to monitor the storage logs regularly.
Besides, maintain disaster recovery plans to adequately manage data during a cyberattack or threat. So, in case of an emergency, you can recover and restore the data.
Regulate Access Controls
HIPAA-compliant software development doesn’t just imply storing the necessary data but also implementing authorized access controls. That helps limit PHI access to the individuals authorized to view and utilize it. When the mHealth software stores data between the physician and patient or between various users, these practices must apply.
HIPAA compliance for software development includes the following:
- Distinct/Unique user access identification
- Automatic timeout or log off
- Encryption
- Data access in case of emergency
- Access monitoring
- Strong user authentication (discussed in the next point)
The healthcare software activity log helps to evaluate in recognizing the unauthorized access. Typically, HIPAA compliance solutions send alerts as notifications so the IT team can take quick action.
Consider Data Disposal (When needed)
HIPAA doesn’t need adequate PHI disposal. But in the case of ePHI, the healthcare app should have the provision to completely purge or overwrite data when needed. It should also be able to physically destroy the data or the device in every form, including backup.
Yet, you’ll have to think of all the archived data and ensure to delete all these backups.
Implement Strong User Authentication
Implementing strong user authentication is important during HIPAA compliant software development. There’s rising evidence that a password is no longer competent and that 2FA (two-factor authentication) using SMS-based OTPs might be prone to attack. But HIPAA should exactly state the usage of particular type of authentication.
So, you can implement advanced access security by using additional authentication for the sensitive interface and short session timeouts. You could also leverage password-less authentication through smart cards, security keys, biometric data, etc.
Secure Software from Internal/External Data Breach
Security policies and technologies still hold an element of human error – human weakness, in nearly every instance, can introduce cyberattack risk. Phishing attacks, lost passwords, unpatched software, or unhappy employees can cause a potential data breach. Hence, it is important to have your software secured and install a good alarm system to stay aware of any issue.
In HIPAA compliant software development, you should ensure that your app provides the following:
- Multi-factor authentication or 2FA or other option for security
- Intrusion detection
- Automatic timeout or logoff
- Maximum security for passwords
Train the employees in all the above-listed elements and comply with them to avoid unwanted issues later.
Ensure Integrity and Audit
HIPAA-compliance software development requires the implementation of administrative and technical safeguards to track activities in systems that use/contain protected data to ascertain integrity. Follow the below points to ensure Integrity and Audit:
- Strong authentication (as discussed above)
- Data transmission security
- Healthcare software architecture (blockchain)
- Digital signature & verification
- Data protection (access control for ePHI)
- Push notification format shouldn’t contain PHI
- System integrity, segregating layers and implementing control on each layer
You could also take the help of a software development company to ensure your software follows all PHI and HIPAA regulations. HIPAA security features keep updating constantly. Hence, periodic audits and HIPAA compliance checklist for software development can help keep your software updated with the latest HIPAA rules.
Have a Remediation Plan in Place
In case of data breach, you need to keep a remediation plan ready to identify the affected users and notify them about the breach. This plan specifies a security tactic that includes the steps business associates must undertake to secure the PHI. Resultantly, it details the best safety practices, covering the below-listed aspects:
- Determine every employee’s duty
- A plan of action to overcome future issues
- A complete list of actions should accomplish to maintain data safety
Consequently, the remediation plan acts as one of the most significant documents for HIPAA compliance application development. However, the major issue is identifying the accurate duties your business requires to meet HIPAA security compliance.
Why is HIPAA Compliance Crucial for Healthcare Professionals?
Data transparency
Every healthcare service provider wants to develop trust between their patients, urging them to declare the fullest detail about their clinical history. Sometimes, people keep away the important information like substance misuse as they don’t know about storing it safely.
The hidden details of a patient have a major effect on long-term diagnosis, which eventually wouldn’t result in appropriate treatment. If the healthcare service provider has implemented complete HIPAA-compliant software development and stores their data securely, they’re likely to provide better patient satisfaction.
Maintaining a positive stature of the institution
Security breaches can prove expensive, not only due to the direct economic expense. The reputation result in case of a data breach outweighs the monetary ones. Your healthcare institution can lose the trust of the patients and investors and may even receive negative publicity.
The public outbreak could be challenging to avoid and control after the organization has undergone a breach. The HIPAA compliance checklist for software development comprises certain practices that let a healthcare institution avoid such risks.
Following HIPAA compliance for medical software applications and receiving a certificate proves the organization’s commitment to patient privacy and data security.
Save additional expenses
Healthcare providers save unnecessary expenses when implementing HIPAA Compliance for medical software applications. HIPAA compliance reduces monotonous paperwork and testing duplication and enhances data security.
Enhanced conversion rate
With HIPAA compliance application development, healthcare professionals can process enhanced medical services to patients. That includes proper diagnosis, minimum data mistakes, reduced chances of privacy breaches, and precise billing. This eventually results in enhanced conversion rates for the business.
Reduced risk of paying large non-compliance penalties
A violation charge can be levied if any healthcare organization fails in HIPAA compliance software development. The HHS has a tool for security risk analysis that any organization can utilize to check for compliance. So, if you aren’t HIPAA compliant yet, HIPAA compliance healthcare software development must be your priority.
What Are the Penalties Under HIPAA-Compliance Violation?
After reading all this, you might wonder, ‘Is it truly worth it to pass through these troubles?
You must aim for HIPAA compliance software development as the HIPAA certification portrays you as an authentic brand within the healthcare sector. It also develops a better and stronger image among medical professionals and the public.
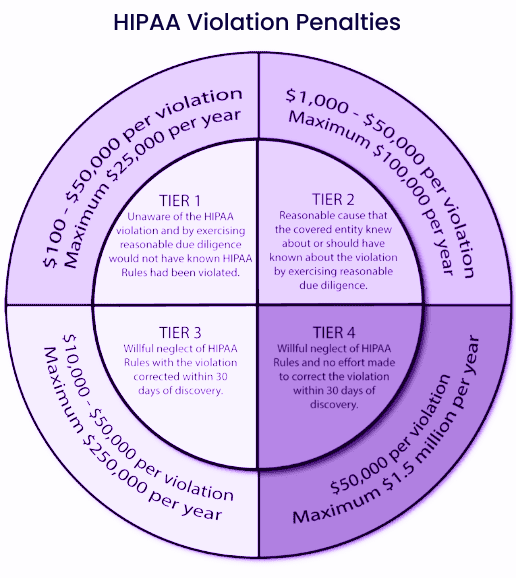
There’s another major reason to opt for HIPAA compliance healthcare software development. If you do not abide by the HIPAA rules and if there’s a data breach in your healthcare app, you’ll have to pay penalties as per the court orders.
Data privacy is your biggest responsibility; thus, you are liable to pay a civil fine between USD 100 to USD 50,000 per HIPAA violation. In case of a security breach of around 1000 user data, you might have to shell out a USD 1000 penalty per user per court order. That equals you paying USD 1,000,000 in this case, no matter how valuable the data is.
What is the Cost of Developing HIPAA-Compliant Software?
A feature-rich HIPAA compliance application development process can cost about USD 50,000 on average. Say, for instance, the cost of HIPAA compliance software development for a telemedicine app can go up to USD 150,000- USD 250,000.
The HIPAA compliance software vendors in Europe charge between USD 25- USD 49 an hour for such service. Meanwhile, the professionals in Asian countries, like India, charge under USD 25 an hour, making them a more viable option.
It might seem that hiring HIPAA compliance software vendors is both difficult and costly. However, safeguarding health data and winning your patients’ trust are of utmost value. Hence, do not avoid HIPAA compliant software development.
Typically, the more complex a health app, the more development steps there’ll be. It takes about four months on average to develop HIPAA-compliant healthcare software.
Also Read – How to Estimate Custom Software Development Costs for Your Projects?
In short, the following factors influence the development cost of HIPAA-compliant medical software:
- The kind of healthcare software, i.e., mobile, web
- Performance requisites for the medical software
- Count of user access (for example, doctors, patients, administrators)
- Compatible mobile platforms (Android, iOS)
- License cost for pre-built HIPAA-compliant software components or cloud services
- Complexity and quantity of characteristics (for example, IoT integrations would increase the development cost)
- Is there a need for additional data storage capacity
- Complexity and number of healthcare IT system interconnections (practice management system, procurement software, EHR, etc.)
- Software/app integration with remote patient tracking tags or monitoring devices
Final Thoughts
If you have decided to make your healthcare app HIPAA compliant, don’t forget to go through this HIPAA compliance checklist for software development. Alternatively, you could hire a professional team with extensive experience creating HIPAA compliant health apps.
Additionally, the HIPAA compliance application development process is no easy undertaking. It needs competence and knowledge, which only top development teams can provide.
eSparkBiz has brought together the best design, development, and testing teams that leverage the latest industry trends to provide top-rated solutions to our clients. Our team takes immense pride in our strong bond with medical entities who trust us in their HIPAA compliance healthcare software development journey.
-
What is HIPAA Compliance?
In a nutshell, HIPAA compliance encompasses meeting the necessary HIPAA requirements and its five associated regulations or rules.
-
What is PHI (Protected Health Information) in HIPAA?
PHI, basically, refers to identifiable patient data, including name, birth date, address, email addresses, device identifiers, imaging results, biometrics, payment information and medical history. When the PHI appears in electronic form, it is referred to as an ePHI.
-
Who are Covered Entities & Business Associates under HIPAA?
As per HIPAA, covered entities are people who work directly with the patients, like insurance providers, hospitals, or physicians. Meanwhile, a business associate is an entity or person that conducts various functions for covered entities, including collecting, storing, sharing, and processing PHI.







